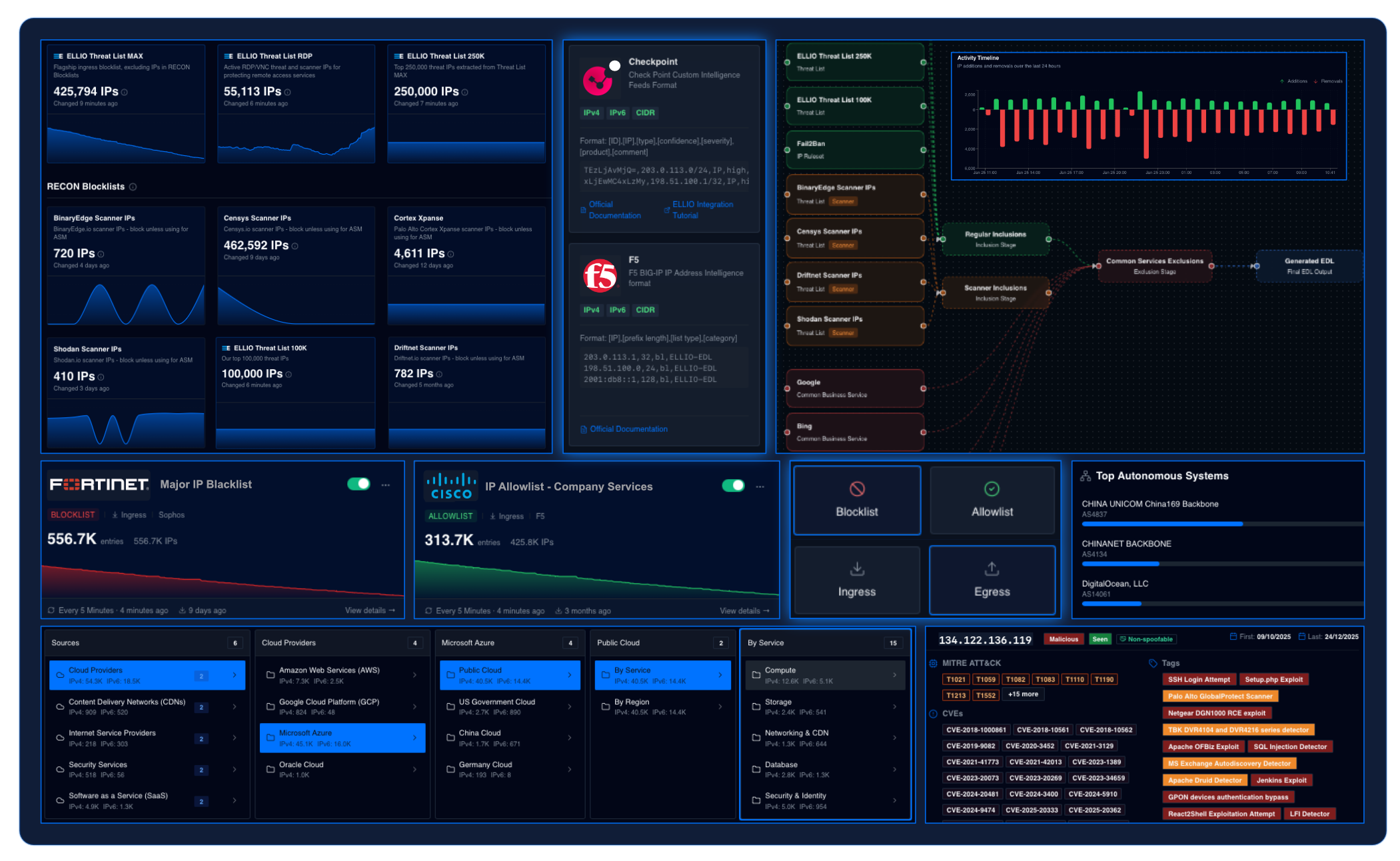
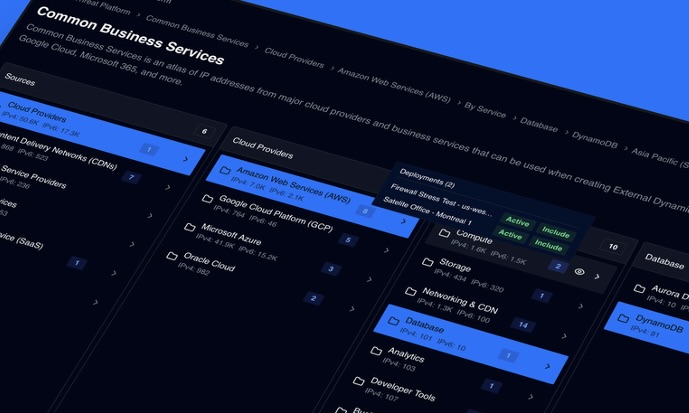
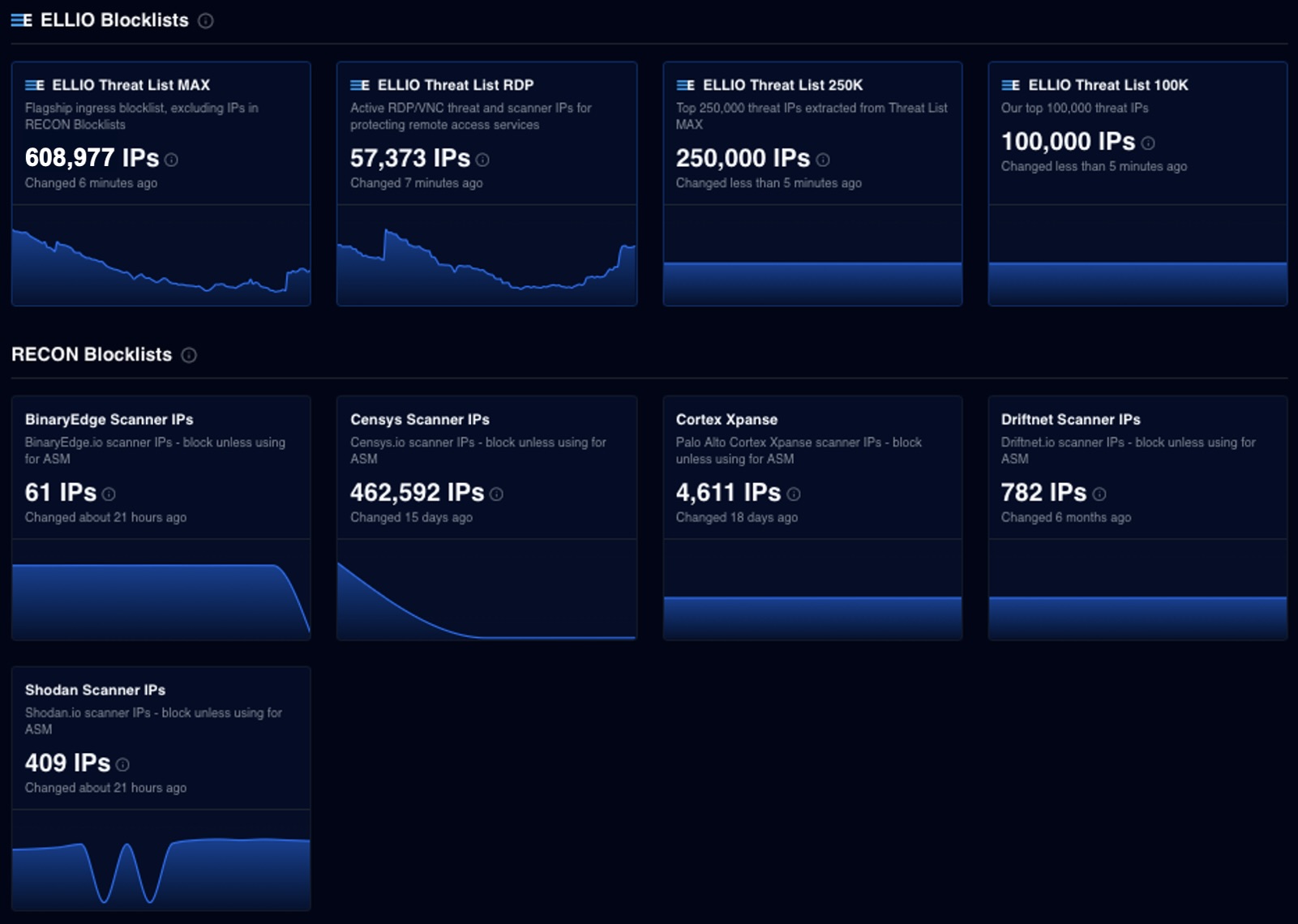
Early action strengthens your entire security stack.

Save resources by stopping attacks before they become costly.
Stop attacks early, during recon, before mass exploitation campaigns hit your network. Save time and resources.

Gain extra time to patch critical vulnerabilities.
Block exploitation attempts before vendor detections exist, gaining extra time to patch critical systems.

See what's urgent faster by cutting noise at the perimeter.
Cut down the volume of alerts coming from XDR, IPS, IDS, and other security tools.

Ensure both security and smooth traffic with zero false positives.
Prevent overblocking and delayed response to new malicious IPs. Automate blocking and keep business traffic flowing.