Detect early-stage threats as they happen.
Detect network scanning, exploit payload delivery, brute-force campaigns, and emerging attack patterns as they unfold, not after compromise.
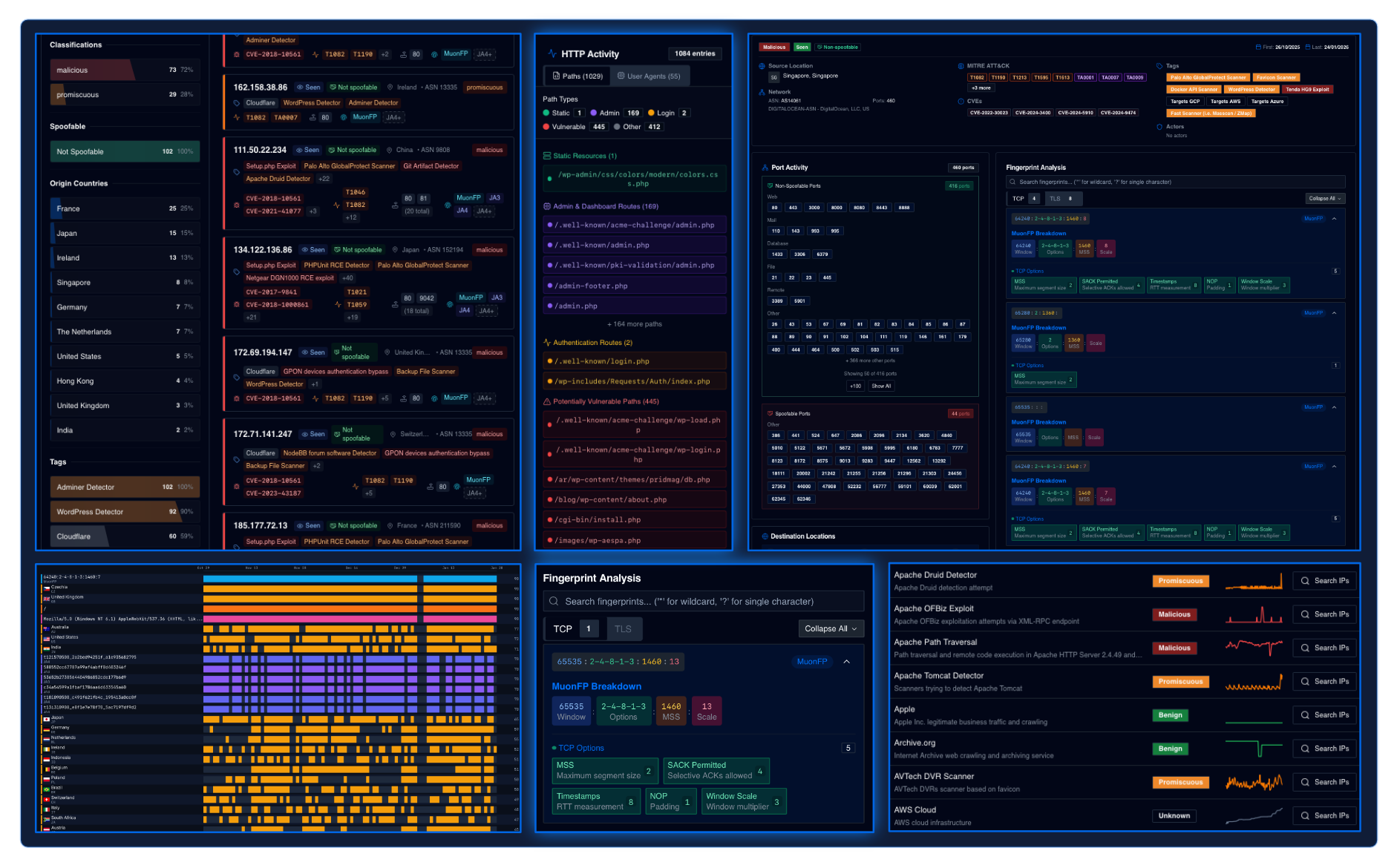
Get the context you need to act early.
Gain real-time visibility into reconnaissance and mass exploitation campaigns across the Internet. Link activity to IPs, fingerprints, exploits, and CVEs. Identify patterns, surface anomalies, correlate infrastructure, and review historical behavior.
See vulnerabilities being actively exploited.
Link live exploitation campaigns to attacker IPs. Map activity to specific CVEs and prioritize the vulnerabilities adversaries are exploiting right now.
See what’s targeting you specifically.
Distinguish attacker infrastructure and campaigns that are explicitly targeting your network from generic Internet noise.
Know exactly what to hunt for.
Correlate MITRE ATT&CK® techniques across IPs and campaigns. Detect reconnaissance techniques (scanning, probing) and identify mass exploitation techniques used for initial access.