
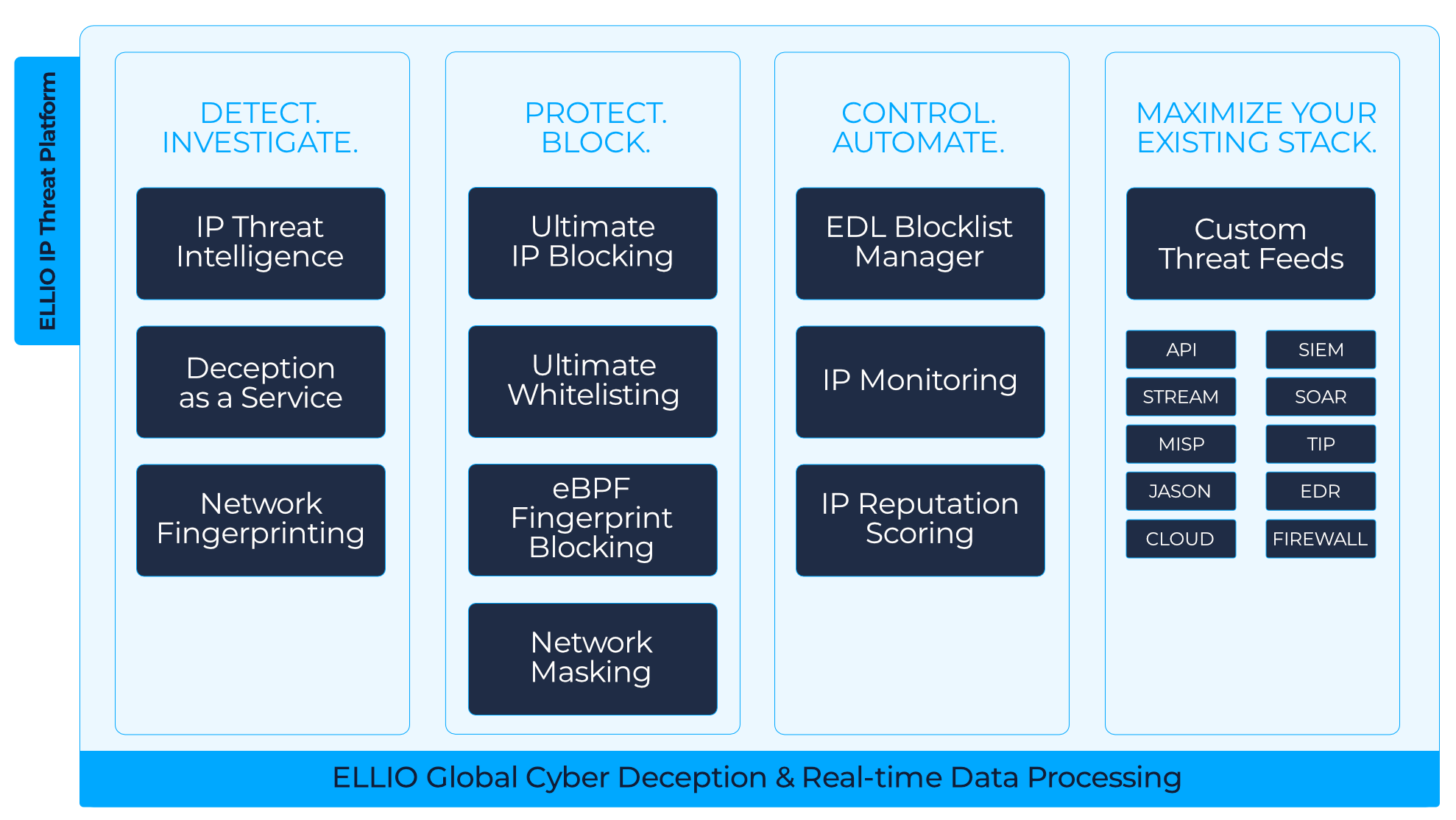
ELLIO IP Threat Platform is an intelligence hub and unified command center for IPs, built for the speed and complexity of today’s AI-driven attacks. Spot threats as they happen, detect patterns, control IP policies, and stop intrusions early. Made for seamless use across cybersecurity, IT, and compliance teams.
Start Free Trial
Splunk, Elastic, QRadar, ArcSight
Cortex XSOAR, Swimlane, MISP, TheHive

ELLIO response system automatically deploys protections across your entire security infrastructure.

Kafka, Pulsar, RabbitMQ, REST/Webhooks.

Correlate every perimeter event with ELLIO's recon & exploit data - pivot on MuonFP& JA4+ signatures to uncover advanced campaigns specifically targeting you.
During a breach, instantly see if an IP reconned your network previously. Use comprehensive metadata to speed forensics and containment.
Gain multi-tenant blocklist control. Offer each client real-time recon/exploit defense, with custom inclusion and exclusion lists.
Stop opportunistic CVE waves in their tracks. Rely on minute-by-minute feed updates to buy patch-teams the time they need.
Deploy on-premises to maintain data sovereignty. Mask your IP footprint and detect nation-state reconnaissance before it can escalate.
Use ELLIO to monitor your cloud IPs for malicious activity. Ensure your infrastructure isn't being used for attacks and protect your reputation.
Discover limited-time prices for Summer 2024.
Discover limited-time
prices for July 2024.